How MaaS affects your business and why you should care?

Malware-as-a-Service (MaaS) is reshaping cybercrime, making advanced attacks accessible to anyone. Learn how MaaS puts your business at risk — from ransomware to phishing — and why proactive security is essential.
The AI Arms Race in Cybersecurity: Defense vs. Offense in the Age of Intelligent Threats

Artificial intelligence is transforming cybersecurity on both sides of the battlefield. While defenders use AI to detect threats and automate response, attackers are leveraging it to craft smarter, faster attacks. This article explores the growing AI arms race and what it means for the future of digital defense.
Why Most SOCaaS Solutions Fall Short — and How We’re Doing It Differently

As cyber threats grow in speed and sophistication, many SOCaaS providers are struggling to keep up. From slow onboarding to limited scalability, traditional solutions often fall short of real-world needs. In this article, we explore the common gaps in today’s Security Operations Center as a Service landscape—and how our next-gen SOCaaS delivers faster deployment, proactive defense, and global, scalable coverage without vendor lock-in.
Kettering Health crippled by ransomware: 14 hospitals on emergency reroute

On May 20, 2025, Kettering Health’s network was hit by a ransomware attack, forcing 14 hospitals to switch to emergency reroutes and manual operations. The attack spread rapidly across critical systems due to undetected lateral movement, highlighting gaps in early threat detection. Patients reported suspicious calls, indicating potential data misuse. This incident underscores the urgent need for healthcare organizations to strengthen identity security, implement layered defenses, and prepare robust response plans.
Western Alliance Data Breach Tied to Cleo Software Flaw

Western Alliance Bank confirmed a data breach in April 2025 linked to a vulnerability in Cleo Integration Cloud. The breach, attributed to the Cl0p ransomware group, underscores the growing risks from third-party software vulnerabilities. Learn how the bank is responding and the increasing role of SOC in protecting financial institutions.
DBS Data Breach 2025: Ransomware Attack Exposes 11,000 Customers

An insights article examining the 2025 DBS data breach, focusing on how a ransomware attack on vendor Toppan Next Tech exposed thousands of customer records, and what it reveals about the growing threat of third-party supply chain vulnerabilities in the financial sector.
Continuous Threat Exposure Management
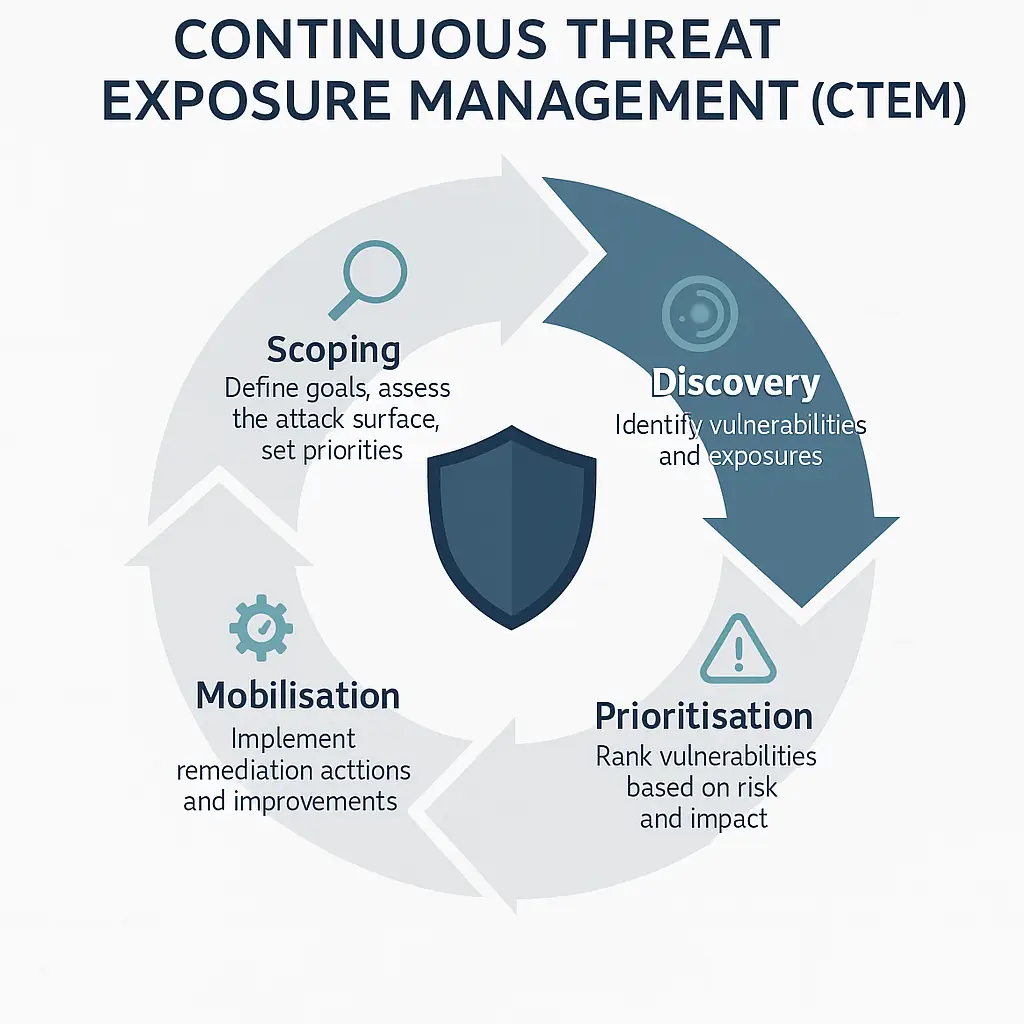
In an era where cyber attacks are not a question of if but when, Continuous Threat Exposure Management has emerged as a crucial strategy for staying one step ahead. For IT directors and C-suite executives, CTEM offers a little easier sleep at night.
Open-Source Tools for SOC Analysts

Security Operations Centre (SOC) analysts leverage various open-source tools to monitor threats, investigate incidents, and automate responses. Below is a structured list of commonly used open-source tools, categorised by their primary function. Each tool’s core capabilities, typical SOC use cases, notable strengths, and integration support are described in formal British English. Security Information and Event […]
PCI DSS 4.0: Significance for Retailers and the Value of SOC-as-a-Service

Every credit card swipe or tap is a moment of trust in today’s retail environment. Customers trust their payment data is safe, and businesses rely on standards to uphold that security. PCI-DSS – the Payment Card Industry Data Security Standard – is the cornerstone of protecting cardholder information. This industry standard, governed by the major […]
SOC365: The Backbone of SOC as a Service

UK Cyber Defence’s SOC365 is a cutting-edge Security Information and Event Management (SIEM) service platform that forms the backbone of the company’s SOC-as-a-service offering.
