Building on our understanding of threat hunting’s strategic value, this section will examine structured frameworks and methodologies essential to successful threat hunting. Establishing robust processes ensures consistent and repeatable outcomes, improving detection accuracy and ensuring thorough coverage of potential threats.
Introducing Mitre’s ATT&CK Framework
One of the most widely respected threat-hunting frameworks is MITRE ATT&CK, a comprehensive model detailing attacker behaviours through Tactics, Techniques, and Procedures (TTPs). ATT&CK provides security teams with a structured reference to understand attacker methods, enabling targeted investigations based on specific adversarial tactics. For example, when conducting hunts focused on Initial Access, analysts may specifically investigate signs of spear-phishing campaigns or vulnerabilities exploited in public-facing applications, correlating these insights with ATT&CK-documented techniques.
Similarly, Persistence tactics within MITRE ATT&CK guide threat hunters to search meticulously for subtle signs of compromise, such as attackers creating scheduled tasks, manipulating registry entries, or exploiting startup folder vulnerabilities. Cyber Defence recently successfully applied this approach in a hunt targeting persistent threats within a large enterprise network. By aligning data collection and analysis with Persistence techniques outlined in ATT&CK, our team efficiently identified malicious registry entries and scheduled tasks, promptly neutralising a hidden attacker presence.
The Pyramid of Pain
Complementing ATT&CK, David Bianco’s Pyramid of Pain offers another invaluable conceptual tool in threat hunting. The Pyramid categorises threat indicators based on adversaries’ difficulty in modifying or bypassing them. At the pyramid’s base are easily modified indicators, such as hashes and IP addresses, which are helpful for short-term detection but offer limited strategic value. Moving upward, indicators such as domain names and network or host artefacts provide more substantial detection potential due to the more significant effort required by attackers to change them.
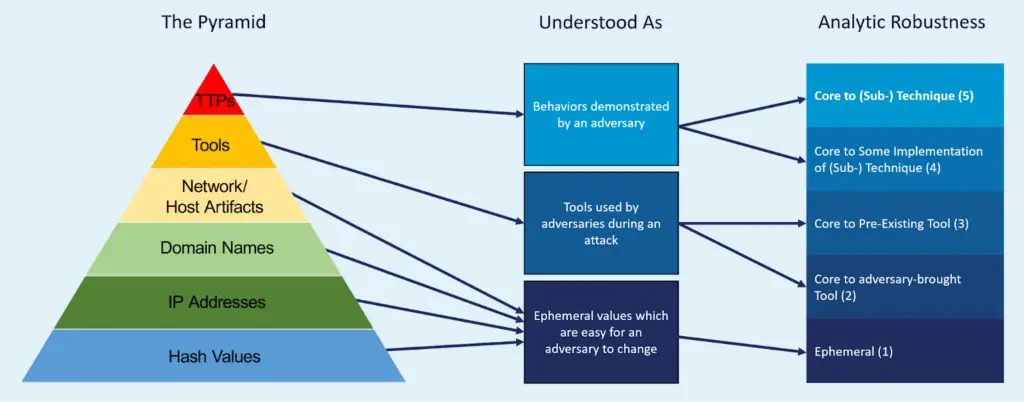
Tools, Tactics, Techniques, and Procedures (TTPs) reside at the highest level, representing the most impactful indicators on threat actors’ operations. Focusing on these high-value indicators forces attackers to fundamentally alter their strategies and methodologies, significantly disrupting their operations. Cyber Defence regularly leverages the Pyramid of Pain by prioritising hunts that target adversary tools and TTPs, resulting in highly effective threat disruption and proactive risk mitigation.
Effective threat hunting typically utilises two principal methodologies: hypothesis-driven and data-driven approaches. Hypothesis-driven hunting starts with well-defined, intelligence-informed assumptions about potential threats. For instance, threat hunters might hypothesise that attackers utilise compromised credentials to conduct lateral movements during off-hours, focusing investigative efforts accordingly. Conversely, data-driven hunting involves extensive analysis of large datasets without predefined assumptions, uncovering previously unknown threats through anomaly detection and behavioural analytics.
Combining these methodologies creates a balanced and comprehensive hunting strategy, capitalising on structured hypotheses and explorative data analysis. This dual approach ensures comprehensive threat detection, enhancing organisational resilience.
Playbooks
Organisations must develop detailed playbooks outlining precise objectives, methodologies, and investigative paths to ensure repeatable success in threat hunting. Effective playbooks clearly define the goals and hypotheses guiding each hunt, specify step-by-step data collection and analysis procedures, provide structured decision-making trees, and detail documentation requirements to capture key findings and insights.
A Case in Point
At Cyber Defence, we recently created a detailed threat-hunting playbook focused explicitly on credential theft detection. This playbook defines exact data sources, such as authentication logs and PowerShell execution records, and details analytical techniques, including anomaly detection and behavioural profiling. It further outlines explicit response actions, such as credential revocation and endpoint isolation, providing our analysts with structured and clear guidance for swift and effective incident response.
Organisations seeking to strengthen their threat-hunting capabilities should actively adopt and tailor frameworks like MITRE ATT&CK and the Pyramid of Pain, develop comprehensive hunting playbooks, and consistently review and update their methodologies based on emerging threats and intelligence. By embedding structured frameworks and methodologies into their security practices, organisations significantly enhance their ability to identify and neutralise sophisticated threats proactively.
In Part 3 of this series, we will explore the essential tools and technologies crucial for conducting effective threat hunts, empowering security teams with practical knowledge to enhance their threat detection capabilities.